Building a Digital Transformation Strategy Part 3
Part 3: Fortify Your Digital Backbone
The human spine is a remarkable feat of evolutionary engineering: 33 individual bones cushioned with fibrocartilage discs, bound together by interlocking joints and ligaments and connected to muscle by tendons. It’s a delicate balance between the rigid structure needed to support upright movement, the strength to protect sensitive nervous tissue, the insulation to absorb mechanical impact and the flexibility to bend and reach.
An organization’s IT infrastructure is its Digital Backbone—the support system for all business operations—and it must strike the same delicate balance: sturdy enough to safeguard internal assets from outside threats, but not so rigid it’s immovable or, worse, it breaks.
The beauty of the human spine is that, while each region and even each vertebra is uniquely designed to perform a specific function, they share the same basic structure and work together harmoniously. The Digital Backbone must manage to do the same, even as the scope of demands placed on it increases.
Middle market organizations are in the midst of digital transformation, an evolutionary response to the disruptive forces of rapid technological, competitive and market changes. Today’s digital economy is one of accelerating connectivity and complexity, rife with opportunity to create and capture value in new and exciting ways. But that opportunity comes with significant digital risk: massive volumes of ungoverned data, more interdependencies, relentless cyberattacks, devastating privacy breaches and new regulations with hefty penalties, as well as the existential threats of automation, commoditization and capricious customer expectations. We now live in a continuous state of persistent threat. And there is less time than ever before to react and respond.

Digital 3+1
At its core, digital transformation is the application of today’s digital advancements in technology to solve traditional business problems, as well as a tool to combat competitive pressures and economic headwinds. How that actually translates into strategy depends on a combination of internal and external factors that will vary from organization to organization. While every company must follow its own trajectory, we can generally break down digital transformation into three primary strategic drivers, as outlined in BDO’s Digital 3+1 approach:
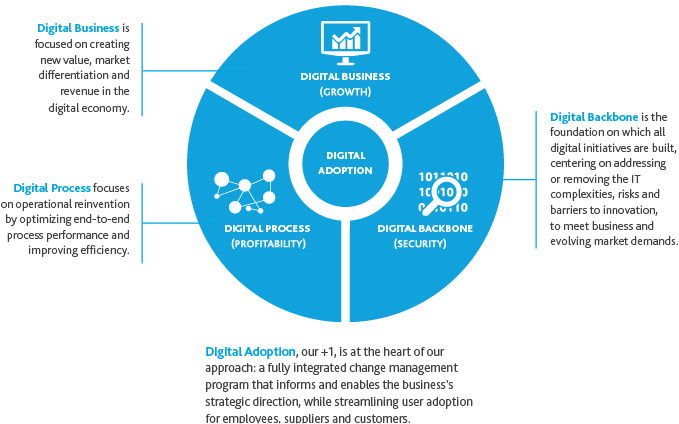
While the Digital Backbone doesn’t lead transformation, it enables it—or alternatively, hampers it. It is inextricably linked with Digital Process; much like the human spine, any weakness or strain in the Digital Backbone causes peripheral pain in other core business functions. On the flip side, you can fortify your Digital Backbone by reducing IT complexities, risks and exposure, thereby increasing agility and scalability in response to evolving market conditions.
To understand the role Digital Backbone plays in your digital transformation, ask yourself these questions:
-
Is IT set up to support business innovation and growth?
-
Do I have the necessary controls in place for the current risk environment?
-
Is my legacy IT compatible with current and future business applications?
-
Does IT enable me to make prudent business decisions with confidence?
If you answered “no” to any of these questions, you may need to upgrade your Digital Backbone, driving value for the business in one of these key ways:
Cost Reduction & Efficiency
Goal: Eliminate redundancies, reduce costs and remove barriers to innovation
KPIs: Availability, Response Time, Number of Application Instances, Parallel Overhead, Throughput, System Efficiency, Total Cost of Ownership
IT infrastructure is often a mishmash of disjointed pieces and parts cobbled together over time. The result is overlapping systems and inconsistency—unnecessary complexity that hobbles the business and impedes innovation efforts. Time, dollars and computing power are wasted on running duplicative applications and outdated hardware and software systems.
Setting aside the extra costs of paying to maintain legacy technology, all that middleware and custom code aimed at connecting the old with the new starts to slow the business down. Information systems developed in isolation aren’t designed to talk to each other, resulting in islands of automation and data silos. Even if a new application can execute its primary function, significant value is lost without systems and data integration. One of the biggest reasons digital transformation initiatives fail is because the “digital outside”—the Digital Business layer—isn’t connected with the “digital inside”—the layer that consists of Digital Process and Digital Backbone.
To prevent IT from becoming an innovation bottleneck, simplification is key. Retire vulnerable or unsupported applications, and consolidate those with redundant functionalities or instances. Unravel convoluted structures, rules and processes. Break down information silos by rationalizing “ROT” (redundant, obsolete, trivial) data and introducing data classification syntax and schemas in line with your overarching data and analytics strategy. Connect external applications with internal business systems and integrate disparate data flows and IT functionalities, including those from third-party software providers.
To stop complexity from building up again, implement a unified set of standards, tools and architecture to create consistency when provisioning and configuring new applications. Removing these IT complexities speeds up the time to market for new business capabilities.
What is an information management strategy?
An information management strategy sets a common vision to align data with current and future business objectives, not only in terms of operations but in terms of outcomes. Key elements of this strategy include:
-
Establish a standard syntax or “data glossary” for cataloguing structured and unstructured data (i.e., metadata)
-
Establish rules and policies for how data is accessed, stored, retained and disposed
-
Set metrics for measuring the quality and usability of data assets
-
Diagram current data flows and track data lineage
-
Have a clear understanding for current and future data and analytics use cases
-
Develop an adaptable data reference architecture
-
Determine data storage needs to facilitate information sharing and data integration
-
Build predefined models for self-service analytics
BDO Case Study
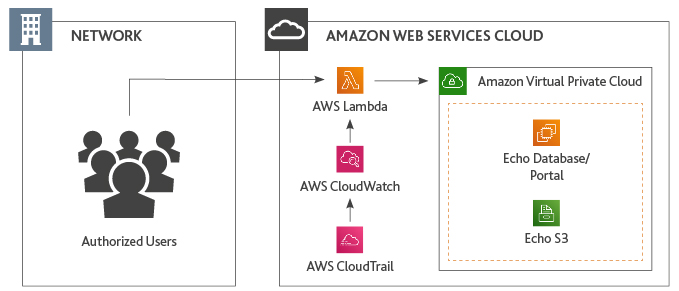
A behavioral nonprofit organization assisting individuals with intellectual and behavioral challenges, had stored Electronic Health Records on an antiquated, unsupported server, running on obsolete hardware that could no longer be patched. Though the company had already moved to a new system that did not require the integration of the legacy data, the records needed to remain available to patients on request for several more years, as mandated by HIPAA retention requirements. The nonprofit approached BDO to help the nonprofit leverage the cloud to keep its data accessible, as part of a broader digital transformation journey to modernize and secure its IT infrastructure and provide donors and beneficiaries with information assurance.
BDO helped to identify the right cloud solution for their needs based on their security, compliance and budget requirements—in this case, Amazon Web Services. BDO then developed a reporting portal, using a security-first architecture including encryption for data at rest and in transit—a necessary measure given the sensitivity of the data and stringent regulatory rules. Even though BDO lacked access to the underlying source code, the team was able to migrate the database from the legacy application to the new user-friendly web portal.
With the implementation of the web portal, the company no longer needs to worry about patching the application or troubleshooting unexpected issues. Resources that would have gone to ongoing maintenance and upgrades have been reallocated to more strategic initiatives. The new web portal also offers enhanced reporting capabilities and enables faster response times to patient requests.
Flexibility & Scalability
Goal: Quickly enable and scale up new capabilities
KPIs: Productivity, Resource Usage, Predicted Capacity, Speedup, Design Time, Runtime, Time to Market
While IT consolidation can go a long way to increase speed and system capacity, you will likely need to modernize your IT infrastructure to enable future digital capabilities and meet increasing service level expectations. Modernization isn’t just about upgrading your legacy technology; it requires evolving your overarching IT and data architecture—leveraging modern application integration paradigms, accommodating new development approaches and tools, and factoring in self-service needs and cloud-native workflows.
Migrating on-premise assets to the cloud is, at this point, practically a requirement. Analyst firm Gartner is predicting the end of the traditional, on-premises data center, forecasting that by 2025, 80% of organizations will move their data centers to colocation, hosting or the cloud. Not only does cloud migration reduce reliance on physical hardware, it offers immediate speed, scalability and security. The cloud is also the gateway to containers and microservices—relatively new cloud-native technologies that can significantly accelerate app development. The cloud has also given rise to “back office-as-a-service” via serverless computing, which allows developers to focus on developing code rather than code execution.
Many IT tasks can also be automated, freeing up resources to focus on service delivery instead of system administration. Patch management, for example, can be automated. Machine learning and AI tools can even be used to automate information governance, from aggregation and cleansing all the way through to extraction in an analytics-ready format.
Digital Resilience
Goal: Mitigate risk, enhance security and improve responsiveness
KPIs: Reported Incidents, Known Vulnerabilities, Inherent Risk Levels, Residual Risk Levels, Percentage of Key Risks Monitored, Cost per Incident, Mean Time to Detect, Mean Time to Resolve, Absorptive Capacity
As data becomes increasingly boundaryless and external digital threats proliferate, the notion of “digital resilience” is often used interchangeably with IT security. To be sure, the high costs of data breaches and a host of new regulations with heavy penalties have elevated its importance to the top of the boardroom agenda. And, in an era of cloud networks and the Internet of Things, data can be spread across an expansive network of partners and vendors, increasing the number of attack vectors for bad actors.
The unfortunate reality, however, is that no wall is impenetrable—and threats are just as likely to come from inside the business as from outside, whether due to human error or malicious intent. Resilience investments need to focus on proactive threat intelligence, detection and rapid response, in addition to basic data privacy and security measures. A more mature security function will continuously monitor external threats and automate threat detection and response accordingly.
Moreover, security defenses can reach a point of diminishing returns—when they become so cumbersome that they impact usability. Think again of the human spine—would you trade a few days of back pain for a lifetime of less mobility? To strike the right balance, assess security and privacy risk at the onset of any new process or development of technology to ensure strong controls are factored into the user experience from the very beginning.
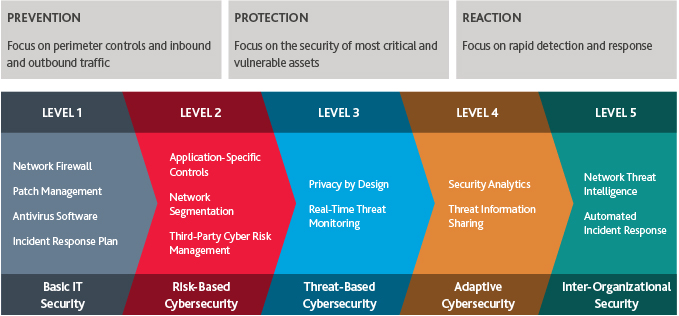
Automation to Support CCPA Compliance
Effective January 1, 2020, the California Consumer Privacy Act (CCPA) builds on existing privacy law principles that prohibit unlawful, opaque, and indiscriminate capture and processing of personal data. The Act is intended to give consumers greater ownership, control and security of their own data in the following ways:
Ownership
Businesses must provide consumers with the categories of information collected about them, their devices and their children, upon request; they must also stop collecting this information, if asked. Businesses that intend to sell consumers’ personal information must also inform them of the categories of personal information they are selling and to whom they are selling it.
Control
Businesses cannot discriminate against consumers if asked to stop sharing or selling their personal data. This includes charging that consumer more, denying them access to services, or changing the quality of the service rendered.
Security
Under current California law, businesses are required to implement “reasonable security measures” to safeguard Californians’ personal information. The Act increases the fines and penalties for violations of the existing law, so businesses are held more responsible for safeguarding consumers’ personal information.
You don’t have to have a physical presence in California to fall under the CCPA’s jurisdiction. If your business collects the personal information of California residents, their households or electronic devices, the CCPA will likely apply if your organization meets one of the following criteria:
-
Have annual gross revenues over $25 million
-
Earn 50% or more of revenue from selling consumers’ personal data
-
Buy, receive, sell or share the information of 50,000 or more consumers, households or devices
If the CCPA applies to you, then you may want to supplement your compliance approach with automation. Start by understanding the breadth of the personal data collected, used, sold or stored. Consider leveraging data discovery and analytics tools to identify and map where personal data resides. These tools can save time and money in developing and maintaining data inventories—critical components of any data privacy program.
To operationalize compliance, centralized tracking mechanisms and data analytics tools can be used
to streamline the management of consumer data requests. Using standardized workflows, integrated Application Programming Interfaces and robotic process automation, you can systematically process requests in a shorter period of time, providing consumers with faster request resolution.
BDO Case Study
In response to a privacy breach, one of BDO’s clients needed a fast and reliable way to respond to the European Union’s General Data Protection Regulation (GDPR) data subject requests. Even though the client was meeting deadlines, the arduous manual process to provide customers with a response to their individual rights requests was time-consuming and costly—and the total number of requests received was about to increase significantly.
On a tight project timeline—under one month to set up, test and demo the technology—BDO delivered a robotic process automation system—a series of bots—that analyzed the database containing the compromised information and quickly pulled the relevant information into a full report for the client’s customers. BDO also created “baby bots” to perform quality control on the main reporting bot, checking the work, identifying any issues or errors, and preventing interruptions.
The bot system was able to do the work of what would have taken hundreds of employees thousands of hours. Not only was the client able to resolve 25,000+ individual rights requests within a short timeframe, they were able to avoid regulatory fines.
Business Insight
Goal: Increase speed-to-decision and enable innovation
KPIs: Total Compliance Operating Expense, Decision Velocity, Decision Quality, Adaptive Capacity
To unlock your organization’s full digital transformation potential, the Digital Backbone should not just stay out of innovation’s way, it should actively facilitate it. That means not just stripping out unnecessary complexity, but fundamentally reimagining back-office functions.
Security and, more broadly, risk management can be transformed into a source of competitive advantage by capturing hidden efficiencies and improving strategic decision-making. Leveraging AI to continuously monitor not just direct threats but the broader threat environment enables the business to shore up critical vulnerabilities as well as anticipate future risks and exploit them. That risk intelligence also helps develop a more accurate understanding of risk tolerance that can inform every business decision. Greater risk transparency encourages more cross-functional collaboration internally, and fosters trust with external partners and customers. Compliance mandates can even be monetized if you anonymize and repackage compliance data.
Every new Digital Backbone initiative is also an opportunity to drive incremental improvement in data management and provisioning, integrate disparate sources of data, and edge closer to a single source of the truth. According to IBM estimates, 88 percent of all data is “dark,” meaning it is collected but sitting around unused. Systems and data integration, following a cohesive analytics architecture, can enable more sophisticated analytics and machine learning initiatives to turn dark data into value.
Survival of the Fittest
The business world has reached an evolutionary tipping point, one that sees the ascension of those that can hack it in a digital environment and the imminent extinction of those that cannot. As disruption sets in, survival of the fittest will come down to which companies can most effectively leverage technology and adapt quickest to change—exploiting uncertainty as opportunity—while circumventing potentially fatal threats. The Digital Backbone must evolve too, becoming stronger to defend against these emerging digital threats and nimbler to realign with shifting business needs in a rapidly changing environment.
Though we can dissect each component of a Digital 3+1 strategy, the whole is greater than the sum of its parts. What good is a strong spine without a functioning brain or a beating heart? Your organization’s digital transformation journey might start with the Digital Backbone, but to go from digital dabbler to digital business, you need to engage the entire system. Your survival depends on it.
Digital transformation is all about reimagining your business and operations for the digital economy, securing your future today. Find out how we help clients disrupt, innovate and transform.
SHARE