The journey toward robust cybersecurity in the Defense Industrial Base (DIB) has been marked by significant milestones, beginning with the implementation of DFARS 252.204-7012 nearly a decade ago. This foundational clause set the stage for safeguarding covered defense information and responding to cyber incidents, but as threats evolved and compliance challenges emerged, additional DFARS requirements — 7019, 7020, and 7021 — were introduced to strengthen accountability and transparency. Now, with the imminent finalization of the new Cybersecurity Maturity Model Certification (CMMC) rule under 48 CFR, the DIB stands at the threshold of a transformative era in cyber compliance. This evolution reflects hard-won lessons and a collective commitment to securing the nation’s most sensitive data against increasingly sophisticated adversaries.
Emerging Threat Landscape
Over the past decade, the DIB has faced a series of high-profile cyber threats, including Chinese cyber-espionage campaigns like Operation Cloud Hopper (APT10), the exfiltration of sensitive F-35 fighter jet data, widespread network tools vendor supply chain attacks, targeted spear phishing campaigns, and disruptive ransomware incidents. These breaches have resulted in the theft of advanced military technology, exposure of critical research, and operational disruptions, underscoring the persistent vulnerability of defense information systems. In response, DFARS 252.204-7012 mandates that contractors implement NIST SP 800-171 rev 2 controls, promptly report cyber incidents, and rigorously protect covered defense information — measures that are essential for safeguarding national security and maintaining the integrity of the defense supply chain.
Key Regulatory CMMC and CUI Rulemaking Milestones
- 32 CFR Final Rule – Effective since December 16, 2024, the purpose is to ensure that organizations handling controlled unclassified information (CUI) and FCI implement and maintain robust cybersecurity practices commensurate with the sensitivity of the data they manage. The rule outlines the required CMMC levels, assessment procedures, and certification processes, mandating third-party or self-assessments based on the type and criticality of information involved. By codifying these requirements, 32 CFR aims to strengthen the overall cybersecurity posture of the defense supply chain, reduce the risk of data breaches, and protect national security interests.
- 48 CFR Update (DFARS 252.204-7021 – CMMC) – On September 10, 2025, the companion 48 CFR rule (to the 32 CFR CMMC Rule) was published in the Federal Register, setting the stage for CMMC requirements to be formally integrated into federal contracts beginning November 10, 2025. This rule implements DFARS 252.204-7021, mandating CMMC certification for contractors handling CUI and introducing a four-phase rollout to help organizations align their cybersecurity practices with the new standards.
- Future Clause – Federal Acquisition Regulation (FAR) Proposed CUI Rule – Establishes two FAR clauses for CUI and a new SF form for documentation of safeguarding instructions for CUI. Finalization could come as early as 2026, setting an aggressive compliance clock for all federal agencies outside of Department of Defense.
Contract Flow-Down and Clause Awareness
Here are the key DFARS clauses:
- DFARS 252.204-7012 – Requires contractors and subcontractors to provide adequate security for covered defense information on their information systems and to promptly report cyber incidents to the DoD, ensuring compliance with NIST SP 800-171 (Rev 2) cybersecurity standards. Note: This is a subcontractor flow-down clause.
- DFARS 252.204-7019 – Requires contractors to submit a current assessment of their compliance with NIST SP 800-171 cybersecurity requirements to the Supplier Performance Risk System (SPRS) prior to contract award, ensuring transparency of cybersecurity posture for covered contractor information systems. This clause is not a flow-down.
- DFARS 252.204-7020 – Basic, Moderate and High Confidence assessments (DIBCAC required for last 2). Requires subcontractors to report scores; prime is responsible for flow-down enforcement. Note: This has a subcontractor flow-down clause.
- DFARS 252.204-7021 - Mandates contractor compliance with the CMMC requirements at the specified level for contract award, ensuring protection of CUI in the defense supply chain. Note: This is a subcontractor flow-down clause.
- DFARS 252.204-7024 – Introduces government award criteria favoring higher SPRS scores.
Please note that some negative-scoring controls can drop SPRS scores below zero (lowest score is -203), and may impact contract award decisions.
Certification Levels and Certification Lifecycle
The panel walked through the three CMMC levels and related timelines:
- CMMC Level 1 – Annual self-assessment and executive affirmation; typically applies to contractors handling only Federal Contract Information (FCI).
- CMMC Level 2 – Requires third-party assessment against NIST SP 800-171 (Rev. 2); generally a 12–15 month implementation process.
- CMMC Level 3 – Reserved for contractors handling large volumes of sensitive CUI; adds 24 controls from NIST SP 800-172 enhanced controls and is assessed directly by the DoD’s DIBCAC (but OSC must achieve Level 2 certification by C3PAO first).
Once certified at a given NIST revision, organizations remain locked to that revision for the three-year certification cycle. Transition to future revisions (e.g., NIST 800-171 Rev. 3) will require new rulemaking, and likely fresh Class deviations for both DFARS 7012 and the 32 CFR CMMC program.
External Service Provider Roles in the Journey to CMMC Certification
For CMMC compliance, there are different roles for service providers that facilitate your CMMC certification.
- CMMC Service providers:
- Registered Practitioner Organizations (RPOs) perform readiness consulting, gap analysis, and mock assessments. They can prepare but not certify. RPOs can perform CMMC mock assessments and, unlike C3PAOs, can tell you how to remediate open controls. They can even provide remediation (like documentation/policies) for you.
- C3PAOs now have full authority to conduct and issue final CMMC Level 2 certifications without DIBCAC present. C3PAOs can consult and certify, but not for the same client.
- External Service Providers:
- Managed Service Providers (MSPs)/ Managed Security Service Provider (MSSPs) implement compliant infrastructure, manage technical controls, and support ongoing monitoring. Look for MSPs that are skilled in a CMMC-ready reference architecture in Microsoft GCC High, that have CMMC certifications (optional, but beneficial), and that have developed a Shared Responsibility Matrix (SRM) to detail their implemented security controls for NIST SP 800-171.
- Cloud Service Providers (CSPs): CSPs play a critical role in the CMMC by hosting, processing, or storing CUI on behalf of defense contractors. They must demonstrate compliance with applicable CMMC requirements, including implementing robust security controls, providing evidence of their own certification level, and ensuring their cloud environments meet the necessary standards for data protection, access control, and incident response as required by the contractor’s CMMC level.
- Enterprise Resource Planning System Implementors: ERP system implementors are responsible for configuring, deploying, and maintaining ERP solutions that may process or store CUI. They must ensure that the ERP system’s architecture, integrations, and security controls align with the required CMMC level, including access management, data encryption, audit logging, and vulnerability management, to safeguard CUI throughout the system’s lifecycle and support the contractor’s overall compliance efforts.
Achieving and maintaining CMMC compliance requires a coordinated effort among various service providers, each with distinct roles and responsibilities. RPOs and C3PAOs guide organizations through readiness and certification, while external service providers — including MSPs/MSSPs, cloud service providers, and ERP system implementors — play essential roles in implementing, managing, and securing the technical environments where CUI resides. Selecting service providers with extensive knowledge, clear matrices, and a deep understanding of CMMC requirements is critical for defense contractors seeking to protect sensitive data and maintain compliance.
Industry Pressure Already in Play: Primes Are Actively Asking for CMMC Compliance
Prime contractors subject to DFARS 252.204-7012 and CMMC must ensure that subcontractors handling CUI meet cybersecurity requirements. This is typically done by vetting subcontractors through detailed cybersecurity questionnaires and assessments. With the anticipated implementation of the 48 CFR Final Rule for DFARS 252.204-7021, primes will be required to only select team members who hold the appropriate CMMC certification level, potentially excluding otherwise qualified subcontractors who have not achieved certification, to maintain compliance and protect sensitive information throughout the supply chain.
What the Prime’s Cybersecurity Questionnaires May Typically Include:
Excel spreadsheets, online survey forms, or PDF documents usually containing the following questions:
- Current CMMC certification for at minimum Level 2
- If not, plans and timelines for achieving CMMC certification
- Implementation status of NIST SP 800-171 Rev 2 controls
- If POAM items are open, what date the organization expects to reach 110
- If the organization has implemented cyber incident reporting procedures
- Evidence of compliance (e.g., SPRS score, SSP and POA&M documentation)
- Per DFARS 252.204-7020, if the organization has posted its current score to SPRS
Cloud Service Offerings Must Be FedRAMP Moderate Equivalent or FedRAMP Authorized
The DoD issued a memo in early 2024 requiring that all cloud service offerings (CSOs) used to store, process, or transmit CUI in DoD environments must be FedRAMP Moderate or High authorized. Key points from the memo include:
- FedRAMP Authorization Requirement: Any cloud service utilized for CUI must have a current FedRAMP Moderate or High authorization, ensuring the provider meets rigorous federal security standards.
- DoD Impact Level Alignment: In addition to FedRAMP, CSOs must also meet DoD Cloud Computing Security Requirements Guide (SRG) Impact Levels 2 or 4, depending on the sensitivity of the CUI.
- Continuous Monitoring: Cloud providers must maintain continuous monitoring and provide evidence of ongoing compliance, including regular security assessments and reporting.
- Contractual Obligations: DoD contracts must specify FedRAMP authorization as a requirement for any cloud service handling CUI, and contractors are responsible for verifying and documenting the compliance status of their cloud providers.
- Transition Periods: The memo may allow for limited transition periods for existing contracts, but ultimately, all CSOs must be FedRAMP authorized to remain eligible for use in CUI environments.
This directive strengthens the security posture for CUI in the cloud and aligns DoD practices with broader federal cybersecurity standards, helping to mitigate risks associated with cloud adoption in defense-related operations.
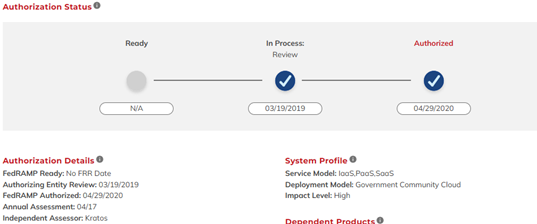
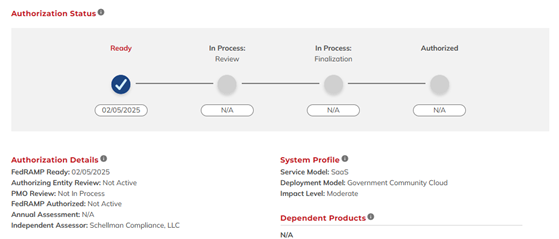
Here are two examples of Cloud Service Offerings listed in FedRAMP that would be considered FedRAMP-compliant for the DoD:
- FedRAMP “Authorized” usually has Federal Agency sponsorship, with “Authorized” being checked:
- FedRAMP “Ready” will only show “Ready” checked and must have a corresponding attestation letter from the FedRAMP 3PAO:
Scoping Strategies and Common Mistakes
Common Scoping Mistakes
- Including the Entire Enterprise by Default: While there are exceptions to this, many DIB contractors find that treating the whole IT enterprise as in-scope instead of isolating only the required minimum systems that handle CUI drives up cost and complexity unnecessarily.
- Improper Data Flow Mapping: Failing to fully trace where CUI is processed, transmitted, or stored can result in liabilities. Overlooking hidden flows (e.g., backups, email archives, logging tools) leads to compliance gaps.
- Not Accounting for Interconnected Systems: Assuming systems “outside” the enclave are out of scope while they remain interconnected (SSO, file shares, remote management, business systems) does not align with CMMC scoping requirements as documented in the “CMMC Scoping Guide.” Per the “CMMC Scoping Guide”, interconnections bring them into scope.
- Unvetted Tools: Users storing or transmitting CUI in collaboration tools (e.g., cloud-based storage, file transfer applications, personal email) that are not authorized for CUI handling and Cloud Service Offerings (CSOs) that do not have FedRAMP moderate equivalency should be removed from the CUI Enclave’s boundary or replaced with a compliant solution.
- Neglecting Scoping the Business Systems (ERP, CRM, HR): Overlooking business systems that may contain CUI/ITAR marked material such as RFIs, RFPs or contracts, especially if hosted in commercial SaaS without FedRAMP Moderate or ITAR compliance, can lead to scope gaps.
- ITAR & U.S. Persons Issues: Not recognizing ITAR data as stricter than CUI, which prohibits foreign nationals (including outsourced IT support) from accessing certain data and requires U.S. data sovereignty can result in noncompliance. Additionally, ITAR data must reside on U.S. soil (U.S. Data Sovereignty).Foreign nationals that serve as systems administrators may have access to all data files – including ITAR, which may cause the business to incur Export Control violations.
Top Scoping Strategies
1. Virtual Enclaves
- Create a logically or physically separate environment where all CUI resides.
- Use segmentation technologies (VDI, VMs, Azure GovCloud, GCC High, AWS GovCloud, or on-prem enclaves).
- Enclaves allow strict control while leaving the rest of the enterprise out of scope.
2. Segregation from Enterprise IT
- Apply least privilege by only granting CUI access to those who need it.
- Separate domain controllers, M365/G365 tenants, and government cloud subscriptions for CUI.
- Use separate SSO or multifactor from the government cloud into the enclave (e.g. do not use one SSO from the enterprise to the enclave as this will violate the physical/logical separation).
3. Minimize Assets In-Scope
- Direct CUI work only into the enclave.
- Use approved collaboration, email, and storage tools only within enclave boundaries.
- Ensure laptops/workstations that access CUI are dedicated or tightly managed.
4. Strict Boundary Controls
- Use firewalls, VLANs, and identity segmentation to enforce isolation.
- Prevent uncontrolled data flows (e.g., backup jobs, monitoring tools crossing the enclave line).
- Implement clear CUI “ingress/egress” controls for uploading/downloading data.
5. Business Systems Planning
- ERP/CRM/HR CSOs that touch CUI must be FedRAMP Moderate equivalent or ITAR compliant.
- If the organization’s ERP cannot meet this, consider dual environments: one enclave ERP for CUI contracts and one for commercial work.
- If business systems solutions are self-hosted on-premise, then the controls configuration responsibilities will be on the organization. If the solution is hosted by a Cloud Service Provider (CSP) on a compliant government/FedRAMP approved platform, , then some of the controls will be inherited/provided by the CSP.
6. Data Discovery & Classification
- Perform full data mapping to identify CUI and ITAR or nuclear data across systems.
- Apply labeling/classification to prevent accidental sprawl into non-enclave systems.
7. Outsourcing Caution
- Ensure MSPs and IT service providers meet CMMC, FedRAMP, and ITAR requirements.
- Prohibit foreign support personnel (unless covered by TAA) if ITAR data is in scope.
- Outsourced IT to other foreign nations must be considered or restricted if it allows full system administrator access to company ITAR data. This may be considered an ITAR potential violation.
Practical Example
- Without Enclave: A contractor’s enterprise email, ERP, file shares, CAD systems, servers and endpoint systems all touch CUI → Entire enterprise IT becomes in-scope.
- With Enclave: Contractor builds a dedicated GCC High tenant + segregated ERP for CUI projects → Only enclave systems are in-scope, leaving enterprise business IT out-of-scope (so long as the organization carefully monitors to keep CUI out of the enterprise systems).
Scoping and Asset Management
One of the most significant challenges is properly scoping all CUI asset types in the CUI environment:
In-Scope:
- CUI Assets – Assets that clearly store CUI. Place CUI into a segregated enclave with FedRAMP Moderate/ITAR-equivalent systems and ensure only dedicated, MFA-protected devices or VDI can access it. All CUI must be labeled, tracked, and monitored to prevent spillage.
- Security Protection Assets – Assets that provide security functions or capabilities and are connected to CUI systems — like MSPs/MSSPs, VPNs, firewalls, SIEM, SOCs, etc. Harden and patch firewalls, SIEM, EDR, and identity services at the same level as CUI systems. Keep them logically separated to avoid accidental CUI exposure in logs or backups.
- Contractor Risk-Managed Assets – These are the systems that typically do not received CUI by policy but can. Restrict these systems from handling CUI and enforce policy and DLP monitoring to prevent misuse. Train staff to keep CUI off corporate email, CRM, or similar platforms.
- Specialized Assets – Systems that may or may not process, store, or transmit CUI but are interconnected to systems that may be CUI assets. Includes IoT, OT, test equipment, etc. Document all IoT/OT/lab systems and isolate those that interact with CUI. If patching isn’t feasible, apply compensating controls like strict access limits and removable media restrictions.
Out-of-Scope:
- Out-of-Scope Assets – Keep these systems physically/logically segregated from CUI environments with no network or data interconnection. Maintain proof of out-of-scope status and periodically validate they remain separate.
Note for CUI environment design strategy: A smaller, well-defined scope not only lowers costs but also shortens assessment timeframes.
Special Notes on ITAR for Cloud Service Offerings (CSOs)
- Microsoft M365 GCC High is required for ITAR-controlled data; GCC may suffice for most basic CUI without U.S. data sovereignty requirements.
- Using multiple cloud providers multiplies the assessment scope via the technical controls for each unique boundary — Using multiple cloud providers multiplies the assessment scope via the technical controls for each unique boundary. Organizations should consider consolidation of their cloud providers.
- Cloud service providers processing CUI must be at least FedRAMP Moderate authorized; MSPs hosting CUI for multiple clients may be considered cloud providers themselves.
- Organizations should be mindful of classifying assets as “out of scope.” If it holds CUI or is directly connected to a system that is, it should be categorized as in scope for CUI because it can receive CUI.
ERP and Business Systems
- Ensure ERP platforms that handle contract data, invoicing, supply chain records, or export-controlled information are scoped correctly.
- Confirm ERP vendor provides FedRAMP Moderate (or higher) equivalency to align with CMMC and DFARS 252.204-7012 cloud requirements.
- Verify ERP system can segregate and protect CUI (role-based access, encryption in transit/at rest, auditing).
- Assess whether ERP customizations or integrations (e.g., with subcontractors or financial processors) expand CUI exposure.
- Require vendor documentation showing incident response, logging, and compliance reporting that meets DoD standards.
ITAR and U.S. Data Sovereignty
- Recognize that ITAR imposes stricter controls than CMMC — data must remain under U.S. jurisdiction and handled only by U.S. persons.
- Ensure ERP systems hosting ITAR data are in U.S.-based data centers with no foreign access pathways.
- Avoid ERP providers that use offshore support teams unless ITAR carve-outs and export authorizations are explicitly documented.
- Validate ERP cloud providers explicitly advertise ITAR-ready or ITAR-compliant hosting.
- Require contractual guarantees that all support personnel are U.S. persons with background checks and access controls.
Outsourced Foreign National Personnel & ERP System Access
- Be aware: Outsourcing foreign national personnel performing invoice processing or ERP support processed in foreign countries may create ITAR violations if export-controlled technical data is embedded in billing or supply chain records.
- Review contracts with accounting or ERP service providers for export control compliance clauses.
- Conduct vendor due diligence on third-party managed services — ensuring that no foreign nationals have access to CUI or ITAR data.
- If outsourcing is necessary, establish segregated non-CUI workflows (e.g., generic purchase orders vs. technical contract deliverables).
Steps Organizations Should Consider
- Map all CUI/ITAR data flows within ERP and connected systems.
- Confirm ERP and business systems meet FedRAMP Moderate baseline or equivalent security.
- Restrict administrative and support access to U.S. persons only.
- Update policies and training for staff, subcontractors, and vendors on handling CUI/ITAR in business systems.
- Prepare evidence for C3PAO assessments — system security plans (SSPs), POA&Ms, FedRAMP authorizations, ITAR compliance attestations.
Future Shift to NIST SP 800-171 Rev. 3 – Should Organizations be Concerned Now or Wait?
While Rev. 2 remains the current requirement (hard-coded to DFARS 7012 by last year’s Class Deviation), Rev. 3 is expected to take effect in two or more years.
Note: The CMMC rollout will take four years to complete, so it is anticipated that there won’t be an effective rollout to Rev 3 until all four phases have been completed.
- Controls reduced from 110 to 98, but assessment objectives increase from 320 to 445 — a roughly 30% increase in complexity.
- Contractors are encouraged to maintain parallel system security plans for Rev. 2 and Rev. 3 to help ensure a smoother transition.
Once certified at a NIST revision (currently Rev. 2), contractors remain locked for three years, even if Rev. 3 is released. Rev. 3 will cut controls to 98 but raise objectives to 445, increasing audit complexity by roughly 30%.
CMMC Recommended Contractor Actions To Take Now:
- Stakeholder Ownership of CMMC Compliance: Maintain stakeholder ownership to ensure compliance remains active and is not merely a “check-the-box” exercise. If C-suite stakeholders are not involved on day one and throughout the project, organizations risk their CMMC progress will stalling and subsequently failing.
- Track regulatory release dates for 48 CFR and Proposed FAR CUI rules: Once 48 CFR is finalized (expected in October of 2025), DFARS 252.204-7021 will begin rolling into new contracts and new option years immediately. There are no current timelines posted for the proposed FAR rule.
- Know the CMMC Phased Rollout Timeline: Plan for phased rollouts of DFARS 252.204-7021. Phase 1 – CMMC L1 & L2 Self Assessments (0-12 months); Phase 2 CMMC L2 certifications required (12 -24 months); Phase 3 CMMC Level 3 certifications required (24-36 months); and Phase 4 rollout will be all requirements to everyone. Army contracts will likely lead this Phase 1 rollout, with other agencies following.
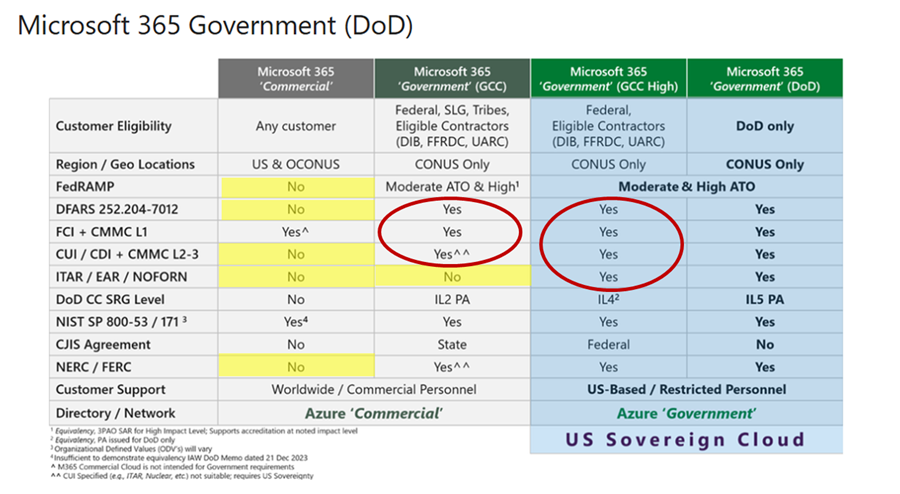
- Cloud Services and FedRAMP: Ensure all CSOs in the CUI boundary are FedRAMP Moderate Equivalent (100% of controls are satisfied) or Authorized. Per Microsoft’s public sector blog for CUI and CMMC found here, Microsoft Commercial 365 (SaaS) is not compliant for CUI environments, as it is no longer FedRAMP compliant and not suitable for DFARS 7012, CUI, ITAR. Microsoft GCC or GCCH (G365) should be utilized instead. DIB contractors may leverage the AWS US East/West or AWS GovCloud (US) based on the requirements of their business and DoD programs and contracts.
- Document and Analyze Cyber Contract Clauses: Conduct contract scoping to map all FAR and DFARS clauses, export control requirements, and ITAR restrictions. Know where CUI touches all IT assets, personnel, and resources.
- Diagram the Organization’s CUI Boundary: Document CUI assets, then logically or physically separate these assets to a segregated boundary to shrink the CUI boundary to a manageable size for certification and future management.
- Engage a Knowledgeable MSP: Engage MSPs that have experience in CMMC reference architecture. The MSP should be able to provide their CMMC certification (if applicable), and their Shared Responsibility Matrix for their reference architecture and how it meets the NIST SP 800-171 controls.
- Leverage Mock Assessments: Use mock assessments by external entities like RPOs to prepare and to provide official external validations SPRS scores before official certification. Use a certified RPO or C3PAO to assess the results. RPOs can offer insight into what controls are open and can even help remediate gaps during their consultation.
CMMC / DFARS 252.204-7021 is approaching quickly, and primes are already enforcing compliance expectations. Contractors are encouraged to act now — by reducing the CUI environment’s scope, securing compliant solutions, and pre-validating CMMC readiness. Those prepared now will not only avoid disqualification from a Prime’s team or a DoD contract, but will help position themselves to have a new differentiator to win more business in a tightening federal marketplace.
Ready to Strengthen Your Cybersecurity and Achieve CMMC Compliance?
BDO’s knowledgeable Cybersecurity Maturity Model Certification (CMMC) team delivers rapid solutions, tailored project plans, and comprehensive CMMC services—including supply chain risk management, contract analysis, and practical workforce training. Let us help you navigate compliance requirements and build a secure, sustainable environment for your organization. Contact BDO today to get started.