The Healthcare Revolution is Here: 8 Predictions for the Year Ahead
From blockbuster deals, to unprecedented medical and technology breakthroughs, there is a major development in the healthcare industry nearly every day.
We see three foundational shifts taking shape: the move from mandates to choice, regulation to competition, and subsidies to actuarial soundness. These moves are driving revolutionary disruption and improving healthcare delivery for patients, providers, payers, drug companies, and investors.Here are the top trends we predict will shape the industry in 2018.
PREDICTION #1
Amazon Becomes Both An ISP and a PBM, Disrupting The Supply Chain As We Know It.
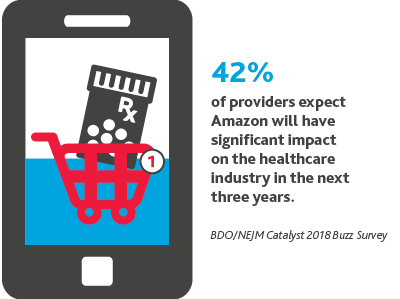.png)
Amazon’s partnership with Berkshire Hathaway and JPMorgan will only be one of its first moves in the healthcare industry.
We believe Amazon will become both an Internet Service Provider (ISP) and a pharmacy benefits manager (PBM). Amazon will use these new roles to both increase drug pricing competition and cement itself as the favored PBM among American consumers.
“People organize their own finances. They arrange their own transportation. They are going to need to own (or own the responsibility for) their own health.”
Lee Jones, CEO, Rebiotix
“The supply chain in healthcare is really now up for grabs. I think it’s pretty clear that Amazon is going to get into this business if you look at the deal now with JPMorgan and Berkshire Hathaway. They are a great master of disrupting supply chain.”
David Friend, MD, MBA, chief transformation officer and managing director of The BDO Center for Healthcare Excellence & Innovation, in CNBC Nightly Business Report
PREDICTION #2
Walmart Enters the Healthcare Industry.
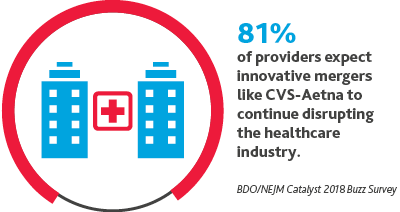
As healthcare focuses on meeting the consumer where they are, we are likely to see retail partnerships.
It’s unlikely that Walmart will sit on the sidelines as competitors like Amazon, CVS Health, and Walgreens explore innovative partnerships. We believe Walmart is likely to enter the space via acquisition and may evolve its personal money management tool so that employees can also better manage their healthcare costs. Other companies will follow its employee wellness model.
“These new entrants are so interesting because they’re not walking into this with the same assumptions that we’ve had in the house of medicine or even in public health for so long. They’re understanding that there are other inputs to health, that there are ways to help people make the right choice when it is available to them. They have a retail approach to being able to customize decision making and the availability of services to meet people where they are.”
Karen DeSalvo, MD, former national coordinator for Health Information Technology, U.S. Department of Health & Human Services
PREDICTION #3
CMS Will Greatly Expand Telehealth Coverage.
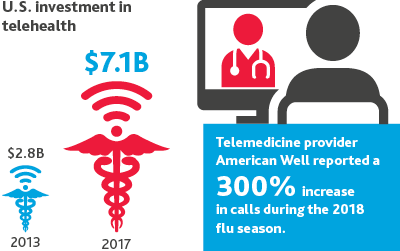
The FDA will continue to deregulate certain mobile devices that help consumers better manage their health.
As Medicare coverage of telemedicine expands significantly under the most recent federal budget deal, the industry will see new companies enter the digital health market at unprecedented rates. Providers will start to prescribe these new devices at greater volumes to improve care outcomes and reduce costs as telehealth coverage expands.
William Payne, MD, CEO, myowndoctor.com
PREDICTION #4
Health Orgs Will Run Late on ASC 606.
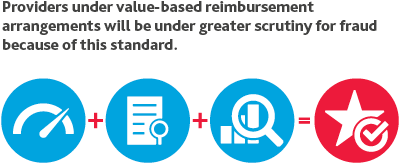 By mid-2018, we expect less than half of healthcare companies will be up to speed with ASC 606, the new revenue recognition standard that went into effect for public entities on Dec. 15, 2017 and will apply for private entities a year later. ASC 606 will require companies to determine revenue recognition based on five steps:
By mid-2018, we expect less than half of healthcare companies will be up to speed with ASC 606, the new revenue recognition standard that went into effect for public entities on Dec. 15, 2017 and will apply for private entities a year later. ASC 606 will require companies to determine revenue recognition based on five steps:
- identifying the contract
- identifying separate performance obligations
- determining the transaction price
- allocating the transaction price to separate performance obligations
- recognizing revenue when the entity fulfills performance obligations
“Under the existing U.S. GAAP reporting requirements, the industry has already struggled to use comparable revenue measures because of the diversity of its constituents. For investors to compare the revenues of a hospital versus those of a skilled nursing facility would be like comparing apples to oranges… When preparing for the new Rev Rec standard, healthcare organizations should first conduct a comprehensive inventory of their contracts, reviewing their revenue cycle management in the process. During this process, they should develop a good understanding of their exposure to value-based retroactive reimbursement.”
Steven Shill, partner and co-leader of The BDO Center for Healthcare Excellence & Innovation, in McKnight’s
PREDICTION #5
Blockchain Comes To Healthcare.
In 2018, blockchain will come to healthcare. 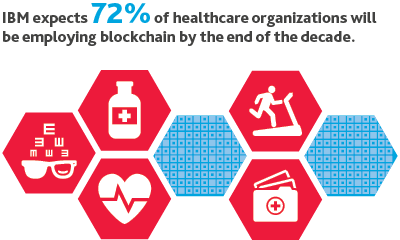
In healthcare’s early blockchain case studies, we’ll see the platform connect health stakeholders across the value chain and improve data transfer and security. Blockchain also holds tremendous potential in managing the volume and veracity of healthcare data, and the platform may help value-based care become a reality.
Change Healthcare, an early adopter of blockchain, announced they will leverage blockchain at scale for their existing claims processing network. The solution they designed can process 50 million transactions per day. To contrast, cryptocurrency Ethereum had 1.4 million transactions in its biggest trading day.
“We need intelligence. We need data. We need high-tech tools to help us [determine] value. Value-based care is not a fad. It is definitely a trend.”
Ann Kraft, MBA, Executive Director, Purdue Pharma
PREDICTION #6
Safety Nets Shutter.

2018 will see safety net hospitals filing for bankruptcy and ultimately shuttering their doors because of CMS’s cuts to the 340B drug pricing program.
Despite legal challenge from the American Hospital Association, America’s Essential Hospitals, and Association of American Medical Colleges, the cuts went into effect in January and are on track to reduce payments by $1.6 billion. While there is debate in the industry about whether the 340B program is achieving its intended goals or ripe for reform, the impact of funding cuts on hospitals and resulting restructuring could be significant.
A January study in the New England Journal of Medicine explored whether 340B was encouraging more physician practice purchases. It found: 340B-eligible hospitals were associated with employing 230% more hematologist-oncologists and 900% more ophthalmologists than hospitals not eligible for the program.
“It's very easy for innovation to support people who have means and access... But if you live in rural Georgia, I think you should still have the same expectation in this country that if you get run over by your tractor, that you're going to have access to quality care and a blood product that's going to be safe... and that your digital record's going to be able to transfer with you when you go down to Emory to have your case done.”
DeSalvo
PREDICTION #7
Brace for the Breach.
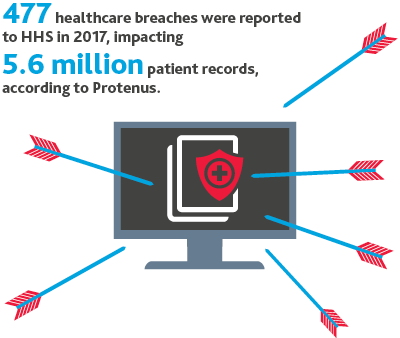.png)
It’s not a question of if but when.
In the coming year, there’s likely to be another major cyberattack on a healthcare organization, and additional guidance from regulatory bodies on data protection and cyber compliance.
Healthcare information is up to 17 times more valuable than credit card data on the black market, as it contains personal health information, personal identification information, and medical research.
And healthcare data has enduring value—it cannot be canceled the way a credit card can.
PREDICTION #8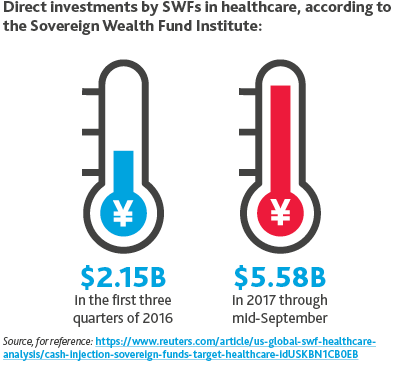
SWFs Up Investments.
In 2018, Sovereign Wealth Funds (SWFs) will increase their investments in healthcare.
One advantage SWFs have over PE firms is that SWFs have patient capital.
Private equity firms must invest their dry powder within a certain timeframe and tend to hold investments for an average of three to five years. SWFs, though, can take a longterm approach, taking their time to identify companies in which to invest and sticking with them for however long is necessary.
The stakes in healthcare are high, and the health of our population is paramount.
For investors, we believe that $10 trillion of wealth will be created in the industry by 2025, but those who invest in the wrong areas stand to lose $4 trillion.Whether you’re leading the revolution in moving care closer to the consumer or more aligned with value—or just along for the ride—the risks are high, but so too are the opportunities.
*Sources: Business Insider (BI) Intelligence, Baker McKenzie, CB Insights, Cisco, Gartner, Grand View Research, International Data Corporation (IDC), MarketsandMarkets, Research and Markets, Statista, World Intellectual Property Organization (WIPO)
SHARE